
Cyber Risk
Increasing global dependence on cyberspace, rapidly and continuously changing technology, sustained vulnerabilities, and advanced persistent threats are driving an increasing societal risk of attack in cyberspace.
Figure 1 quantitatively illustrates a number of strategic trends that characterize the cyberspace domain. For example, static malware signatures are expected to increase from just less than three million today to over 200 million by 2025. At the same time, fiscal constraints will limit resources to counter these threats and drive increased autonomy. By 2025 there will be an estimated 5.5 billion people online using 25 million applications, engaging in billions of interactions per day, and creating 50 zetabytes (trillion gigabytes) of data.
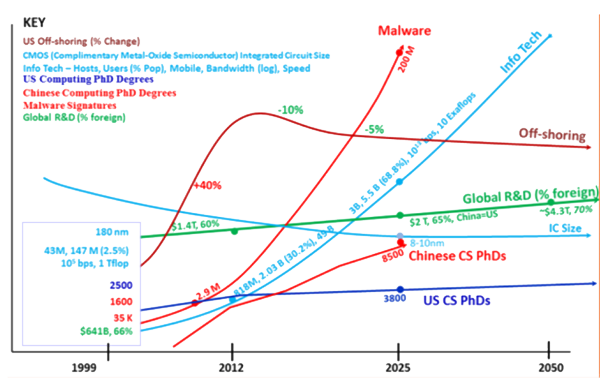
Figure 1: Strategic trends 1999-2025
Given the serious nature of the threat, the US government has imposed mandatory cybersecurity standards on large sectors of the economy. Section 10 of a February 2013 Executive Order requires all agencies with responsibility for regulating the security of critical infrastructure to start a process of developing mandatory cybersecurity requirements based on the National Institute of Standards and Technology (NIST) cybersecurity framework (NIST, 2014). These rules aimed to safeguard unclassified technical information (UCTI) and associated systems will be incorporated in all new DOD (Department of Defense) solicitations and contracts. The term “Adequate security” is defined as “protective measures that are commensurate with the consequences and probability of loss, misuse, or unauthorized access to, or modification of information.” The regulation specifies that, at a minimum, adequate security requires that the IT systems on which UCTI transits or is stored must comply with specified security standards.
Systems engineering is the branch of engineering concerned with the development of large and complex systems, where a system is understood to be an assembly or combination of interrelated elements or parts working together toward a common objective. Past experience has shown that formal systems engineering methodologies have not always been successfully applied to large and complex cybersecurity systems. These complex systems have become commonplace when applying cyberstrategies in cybersecurity operations. The ability to build, operate and maintain such systems is crucial to the effectiveness of cybersecurity operations. Most importantly, a cyberstrategy program must surround these systems on a global scale across multiple inter-related platforms.
Without robust systems engineering methodologies, the realization of complex information systems involving numerous interacting components would be prohibitively expensive, prone to failure and involve timescales unacceptable in today’s cybersecurity industry.
Systems Engineering and Cybersecurity
Systems Engineering. Systems Engineering is defined as an interdisciplinary process that ensures that the customer’s needs are satisfied throughout a system’s iterative life cycle.
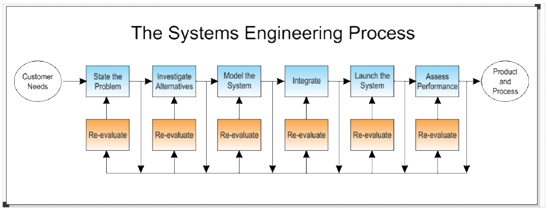
Figure 2: The Iterative Systems Engineering Process
When the system under consideration is something manufactured, like a computer, then its system life cycle usually has seven phases: (1) requirements development, (2) concept development, (3) full-scale engineering design and development, (4) manufacturing and deployment, (5) system integration and test, (6) operation, maintenance and modification, and (7) retirement, disposal or replacement. The system life cycle is different for different industries, products and customers.
The systems engineering process includes, but is not limited to: understanding customer needs, discovering system requirements, defining performance and cost measures, prescribing tests, validating requirements, conducting design reviews, exploring alternative concepts, sensitivity analyses, functional decomposition, system modeling, system design, designing and managing interfaces, system integration, total system test, configuration management, risk management, reliability analysis, total quality management, project management, and documentation.
Cybersecurity. The world of cybersecurity increasingly relies upon critical digital electronic information capabilities to store, process and move essential data in planning, directing, coordinating and executing cyber operations. Powerful and sophisticated threats can exploit security weaknesses in many of these systems. Weaknesses that can be exploited become vulnerabilities that can jeopardize the most sensitive components of information capabilities. However, we can employ deep, layered defenses to reduce vulnerabilities and deter, defeat and recover from a wide range of threats.
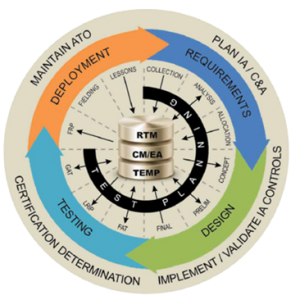
Figure 3: The aggregated lifecycles of system architecture, development, deployment, design, test, configuration management (CM), Certification & Accreditation (C&A), requirements traceability, etc.
